
Just when you think it’s safe to go back into the water, “weaponized sharks” using artificial intelligence (AI) can turn “phishing” into chaos and nightmares for local municipalities. Just like transforming viruses, strains evolve ready to attack the vulnerable. For that reason, it is imperative that vigilant due diligence be respected, taken seriously, and implemented throughout your organization. Historically, thieves have always been one step ahead in a game that continually moves the target because that is what they do. So, protecting your local government by following cybersecurity best practices is potentially more essential now than ever before because today’s thieves can be highly skilled at using AI to get what they want. They just need a little help to get started, and “EvilProxy” is their latest tool of destruction, wreaking havoc on unsuspecting organizations.
What is EvilProxy?
EvilProxy is a phishing tool based on a reverse proxy architecture that allows attackers to steal multi-factor authentication (MFA) protected credentials and session cookies. This rising threat combines sophisticated adversary-in-the-middle phishing with highly advanced account takeover methods, in response to the growing adoption of multifactor authentication by organizations (source: Proofpoint). This relatively new malicious campaign has spread its roots this year as it’s cheap, easy to use, and is being advertised on the dark web as “Phishing-As-A-Service!” It is known to target executives and local governments through sophisticated deception campaigns.
What’s particularly noteworthy is that EvilProxy throws such safeguards as MFA into disarray. Here’s how:
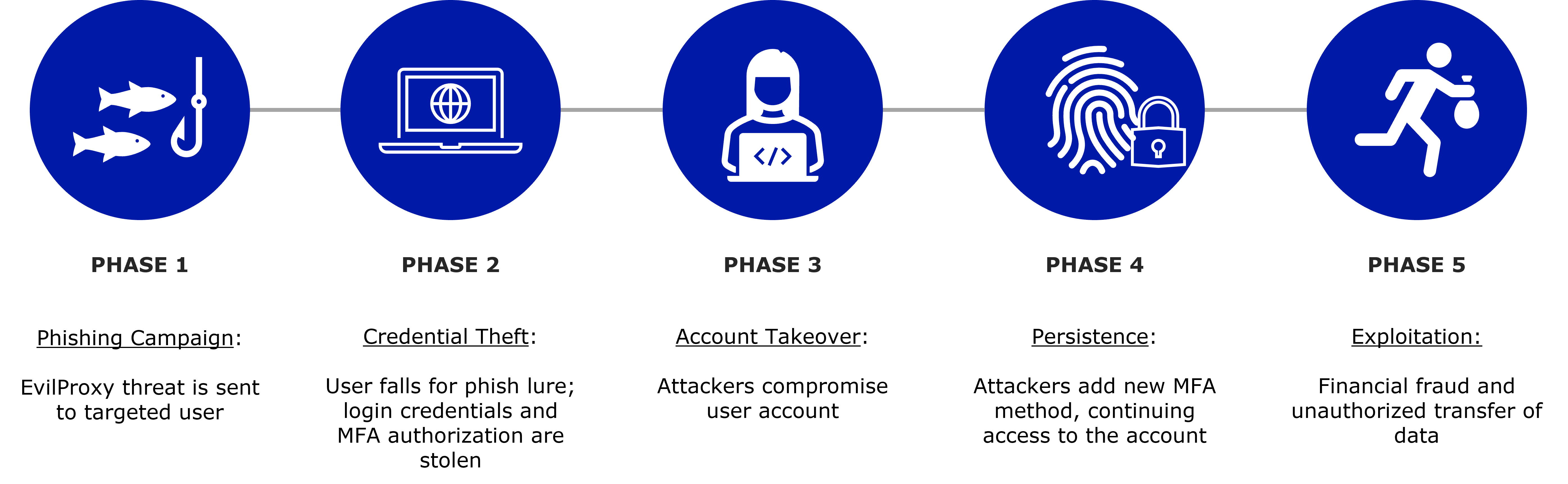
Figure 1: EvilProxy Attack Chain Phases. Content based on information and imagery sourced from ProofPoint www.proofpoint.com/us/blog/email-and-cloud-threats/cloud-account-takeover-campaign-leveraging-evilproxy-targets-top-level
Changes and Account Security Enhancements
Next month, we will be employing updated security protocols to further assist your local government in protecting its TrustINdiana account. As a new, default setting, current Authorized Signers will automatically be “opted in” to receive email notification regarding activity on their TrustINdiana account. Going forward, all contacts will be “opted in,” regardless of their user status (read-only or authorized signer).
In addition, we will no longer accept outdated forms sent to the Client Service team for processing.
For example, this means that when someone sends in a form for a contact to be updated on their account, they must access the most current version of the form in the TrustINdiana Online Transaction Portal. If you need to make an adjustment to your account, please navigate to the “Documents/Forms ” section or Help Center of the TrustINdiana Online Transaction Portal and download the appropriate form for submission to our Client Service team.
You have access to a variety of forms tailored to adjust your account. Here’s a breakdown of the different forms available to you:
- Dual Authorization Form: Allows your entity to sign up for dual approval of transactions.
- Bank Amendment Form: Allows your entity to add/remove banks on file, adjust wire/ACH preferences, etc.
- Contact Amendment Form: Allows your entity to add/remove contacts on accounts and their status i.e., read-only or authorized signer.
- Deposit Instructions: Contains the TrustINdiana deposit instructions so that Participants can send their funds to their TrustINdiana account.
- Name Change Form: Allows your entity to update users’ names on an account i.e., someone just got married and wants to change their last name.
TrustINdiana is committed to account security protocols and continually evolving enhancements; supporting that effort on your behalf is among our highest priorities. Success only happens by working together in this ongoing effort. “Set it and forget it” no longer works or applies, given the likes of EvilProxy and the continuing onslaught of phishing campaigns that lie ahead in the future. We encourage local governments to remain vigilant and take security due diligence seriously.
To learn more about best practices for your local government, here are a few resources:


